Our solutions are tailored to each client’s strategic business drivers, technologies, corporate structure, and culture.
Final CMMC rule: Key details and phased implementation timeline
Cybersecurity Maturity Model Certification takes effect in December 2024. Read about its phases, clarification on ESPs and out-of-scope assets, and more.
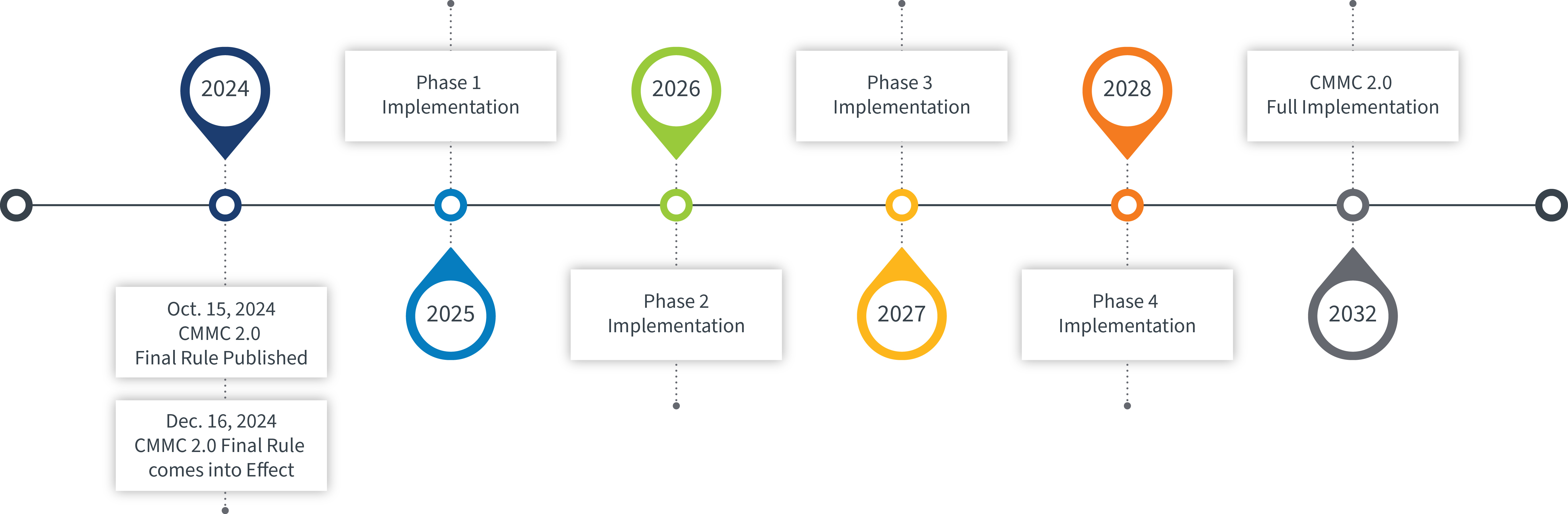
The Department of Defense’s (DoD) Cybersecurity Maturity Model Certification 2.0 (CMMC) rule, published Oct. 15, will become effective on Dec. 16, 2024.
There are very few contractors within the Defense Industrial Base (DIB) that are not familiar with CMMC. However, the complexity of this final rule warrants extra attention to its many requirements and how to prepare.
Below are some major highlights taken from the 470-page rule. We will add notable updates and clarifications as they become available.
Final CMMC implementation phases and timeline
The four-phased implementation plan of the CMMC Program “is intended to address ramp-up issues, provide time to train the necessary number of assessors, and allow companies the time needed to understand and implement CMMC requirements,” the final rule states.
- Phase 1 has been extended by six months and starts with the implementation of this rule and amendments to the DFARS clause.
- Phase 2 will require contractors handling controlled unclassified information (CUI) in most circumstances to undergo a third-party assessment by a C3PAO as a condition of award.
- Phase 3 involves only the DoD – not third-party groups – conducting a Level 3 CMMC assessment for contracts involving the most sensitive CUI.
- Phase 4 is the “full implementation” of the CMMC requirements.
- Phases 2-4 will each start consecutively one calendar year after the preceding phase. However, the DoD’s objective timeline to begin implementing the CMMC requirements has been, and remains, FY2025.
- Full implementation of CMMC by all defense contractors is estimated to occur over seven years.
Clarity on External Service Providers (ESPs)
- ESPs that are not Cloud Service Providers (CSPs) and do not process, store, or transmit CUI do not require CMMC assessment or certification.
- At the same time, an ESP that is not a CSP but does process, store, or transmit CUI will fall within the assessment scope.
- When a CSP is used, it must meet the requirements of the FedRAMP moderate baseline or the equivalent.
Out-of-scope assets
An endpoint hosting a virtual desktop solution (VDI) configured to not permit any processing, storage, or transmission of federal contract information (FCI) and CUI beyond the keyboard, video, or mouse input sent to the VDI client is considered out of scope.
Next steps for an organization seeking certification
Our previous article on the CMMC final rule outlines steps your organization might need to take at this critical point. We have also previously explored categories of contractors, ranging from the CMMC-prepared to the unprepared, and how they can remain or become compliant, maintain their competitive edge within the DIB, and enhance the U.S. warfighter effort.
How CohnReznick can help
As an authorized Registered Practitioner Organization (RPO) and C3PAO, CohnReznick is well positioned to assist members of the DIB in their Cybersecurity Maturity Model Certification with key steps such as:
- Confirming the scope of CUI within their environment
- Reviewing the CMMC framework to understand practices and processes needed to meet compliance
- Conducting a preparedness assessment and/or the actual assessment needed to obtain certification
Contact our team to get started.
Contact
Let’s start a conversation about your company’s strategic goals and vision for the future.
Please fill all required fields*
Please verify your information and check to see if all require fields have been filled in.
Related services
This has been prepared for information purposes and general guidance only and does not constitute legal or professional advice. You should not act upon the information contained in this publication without obtaining specific professional advice. No representation or warranty (express or implied) is made as to the accuracy or completeness of the information contained in this publication, and CohnReznick, its partners, employees and agents accept no liability, and disclaim all responsibility, for the consequences of you or anyone else acting, or refraining to act, in reliance on the information contained in this publication or for any decision based on it.









.jpg?h=400&w=1380&hash=E616C61DE9CB52C77EEB45836E16B3F4)







